- tl;dr sec
- Posts
- Endpoint Finder: A static analysis tool to find web endpoints
Endpoint Finder: A static analysis tool to find web endpoints

Olivier Arteau, Desjardins twitter
abstract slides video source code
After presenting about his new bug class, Prototype pollution attacks in NodeJS applications at NorthSec 2018 (which by the way made it into Portswigger’s Top 10 Web Hacking Techniques of 2018), Olivier needed a better way to analyze JavaScript code at scale.
Existing tools were either dead, regex-based, or didn’t support the analysis capabilities he wanted, so he built and open sourced endpointfinder, which parses JavaScript code into Abstract Syntax Trees (ASTs) to determine the routes that are defined (e.g. $.get() or open() calls on an object of type XMLHttpRequest). These results can by automatically imported via an accompanying Burp or Zap plugin.
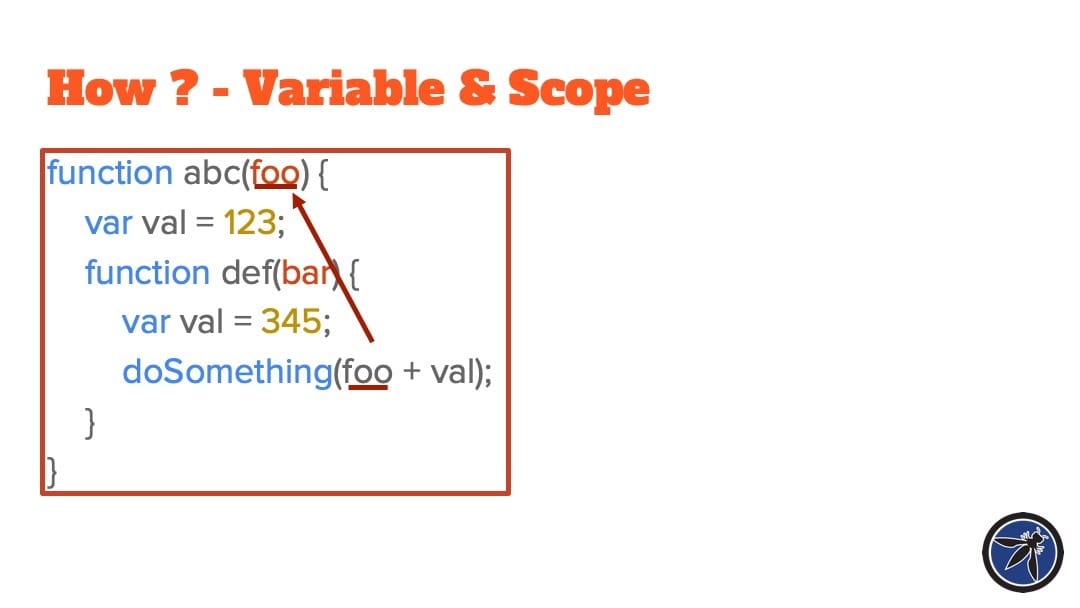

I’m a big fan of the power of AST matching over regex (after all, I gave a talk at ShellCon 2019 about it), so I’m glad this work was done.
That said, I feel like Olivier’s use of the term “symbolic” is a bit misleading (to me, it hints at symbolic execution, which this is not), and I think his use of the term “call graph” is a bit different than what’s agreed upon in the program analysis community.
I like yhis talk, but I think the terminology and approach taken (e.g. when reasoning about variable values and function calls) would benefit from doing a bit of literature survey.
See the summary forThe White Hat’s Advantage: Open-source OWASP tools to aid in penetration testing coverage for a discussion of OWASP Attack Surface Detector, which also uses static analysis to find routes for web frameworks in Java (JSPs, Servelets, Structs, Spring MVC), C# (ASP.net MVC, Web Forms), Rails, and Django.