- tl;dr sec
- Posts
- Leveraging Users’ Engagement to Improve Account Security
Leveraging Users’ Engagement to Improve Account Security
Amine describes how Pinterest protects users who have had their credentials leaked in third-party breaches using a combination of programmatic and user-driven actions. He refers to these users as “high risk users” (HRU).

Balancing Security and User Experience
One thing I liked about this talk is how Amine described the various protection mechanisms they could implement and how Pinterest weighed the security ROI vs the impact on user experience.
It’s easy, as a security professional, to say, “Let’s do this, because it has the best security properties,” when in the real world, we need to be balancing security with the needs of our business and the experience of our users. A perfectly secure business with no users won’t be a business much longer.
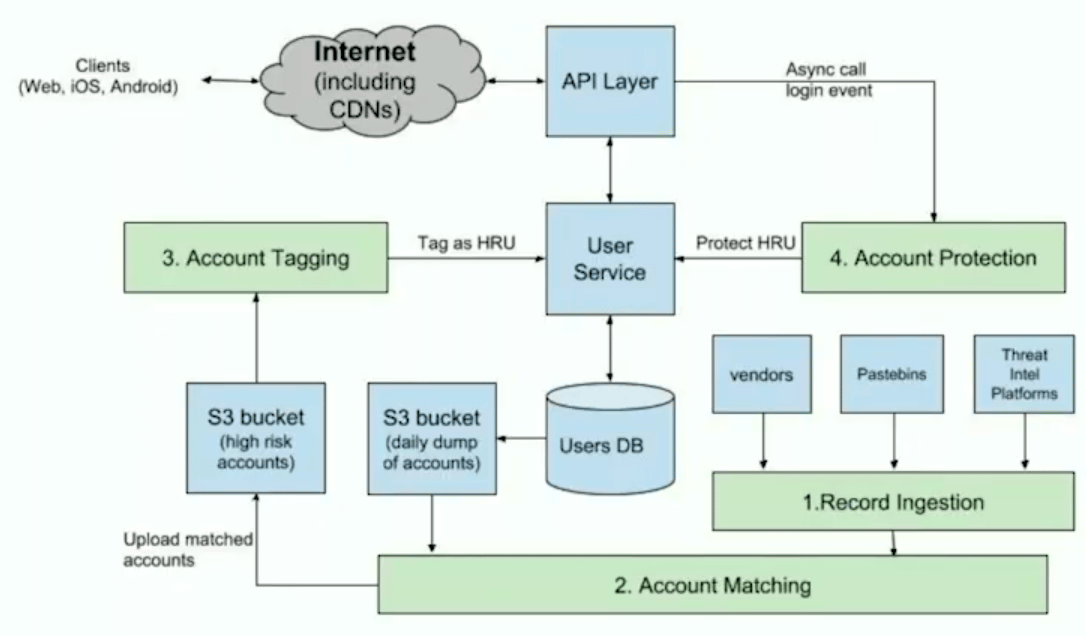
Pinterest’s solution has the following 4 steps:Record Ingestion: Ingest third-party data breach infoAccount Matching: Determine email/password combinations that match Pinterest usersAccount Tagging: Tag accounts as high risk once credentials have been verified to be in useAccount Protection: Protect accounts to prevent account takeovers
1. Records Ingestion
There are a number of sources you can use:
Vendors: Reliable, provide info in an organized, easily parseable format, but can be pricey. (e.g. HoldSecurity, Qintel, Shape)
Public Dumps: Tend to be unreliable, disorganized, and have duplicates. Thus, they require more work to get value from, as you need to verify and clean up the data. (e.g. pastebin.com)
Threat Intel Platforms: These tend to be more for malware analysis, spam, etc., but can be useful here. (e.g. Threat Exchange, AlienVault OTX)
Random Sources: Other publicly available, reporters, underground forums, dark web services and markets.
2. Account Matching
Dump your whole list of users
Somewhere safe, like in a strictly secured S3 bucket that can only be accessed by your matching service.
You can do this at whatever frequency makes sense for your business, for example daily or weekly. Pinterest does it every 3 days.
Structure the user data like:
user_id | email | bcrypted_password
Combine accounts
Filter through the data you’ve ingested and look for emails that also belong to users within your system.
For each matched email address, recompute the
bcrypt‘d password and determine if it matches the value from your database. If so, add it to the list of “matched” accounts.
Upload accounts - upload only the list of
user_idsmatched to an S3 bucket, delete the prior user account list dump.
3. Account Tagging
This process can be challenging, as there are many large files to process and potentially many users per file to tag as being at high risk for account takeovers.
Pinterest’s solution is to have a nightly tagging job that distributes the work over multiple worker threads.
Interesting points:
High risk users are given a Unix timestamp field
credentials_leaked_at, not just a boolean likehas_leaked_creds, because timing matters.They define a
is_high_risk_userfunction, that incorporates if the user has changed their password after when their creds have leaked and if they’ve turned on 2FA.
4. Account Protections
Pinterest uses two classes of account protections: programmatic, enforced automatically by Pinterest, and user engagement-based, which requires active steps taken by users.
Programmatic Protections
Again, the goal is to protect as many high risk users as possible while minimizing friction and providing a great user experience. This comes into play below when determining when and how to protect users.
To protect users they:
Immediately invalidate all active sessions (Have a
session_valid_afterfield so that sessions that predate your protection are no longer valid)Link users to the reset password / recover account flow.
Send the user an email letting them know what happened. They noticed that this is a good opportunity to encourage users to enable 2FA, as users who received this email tend to be more likely to do so.

When should you protect users?
As soon as possible
Next time they log in (don’t affect active sessions)
Pinterest choses the latter, protecting on next login, the intuition being that if an attacker gained access to a user’s credentials, they’d use them to log in, and thus create a new session. They don’t want to affect active sessions unless they have evidence that that account has been exploited.
Within protecting users as they log in, there are two options:
Aggressive approach: each time a high risk user is logging in, protect the account (impact growth)
Balanced approach: correlate with other signals to determine risk. Have we seen this device/browser before? What’s the reputation of the IP?
User Engagement-based Protections
Encourage the user to help secure their account, as we’re not sure if they’ve been exploited.
A benefit of this approach is that you don’t have to invalidate their session and log them out, which is a better overall user experience.
How to do this?

Give users several options to go from an insecure state to a secure state.
As the user is setting a new password, you can enforce that they create a more secure password, in length and complexity as well as ensuring it doesn’t match known breached passwords.
A user can also chose to link their account to Facebook or Google instead. In that case, Pinterest disables password-based logins for that user.
Not Just High Risk Users
You can use this same security nag approach on other high value accounts, such as advertisers, businesses, celebrities, and creators.
Results
On average, they programmmatically protect ~5,500 high risk users per day, or ~170,000 per month.
High risk users choose to secure their accounts by (daily average):
Changing their password: ~1,200 users
Using Google for login: ~1,000 users
Using Facebook for login: ~900 users
Pinterest has observed a 20% engagement rate with the security nag. That is, 1 out of 5 users who see it will go through the full flow of securing their account.
Nice! That’s much higher than I expected.
On average, user engagements adds ~3,100 high risk user protections per day, or 96,000 per month.
Together, programmatic and engagement-based protect ~266,000 high risk users per month.