- tl;dr sec
- Posts
- Intent Over Tactics: A CISO's Guide to Protecting Your Crown Jewels
Intent Over Tactics: A CISO's Guide to Protecting Your Crown Jewels
A practical guide to protecting your most critical assets when budget, head-count, and political capital are tight.
One of the struggles I had as a first-time CISO was that it was now on me to make the company safe. You are asked for a strategy and are faced with this overwhelming thought of, "What is a strategy other than 'secure all the things' and put out all the fires?"
You realize that a strategy has to be practical, have a real impact, make sense, be focused, and be easy to understand for everyone from the executive team and the board, down to the people executing the work. It also has to pass the most important test of all: "Does it make it more expensive for the attacker?" Ultimately, does it help make the company safer?
These are high bars to overcome. In a world in which you have 1,000 holes you constantly have to plug, coming up with this is a monumental task. You cannot just create something that the board members nod "yes" to, but also something that the most experienced red teamer in your org says, "Yes, this makes sense," as well. I struggled quite a bit to find the thing that matters the most and ultimately ended up with the crown jewels strategy (among many others which I mention at the end and will have their own separate posts).
This guide provides a comprehensive framework for creating, pitching, and implementing that strategy within your organization.
Why Does This Strategy Make Sense?
First, let’s start with the "Why." Why does this make sense? Ultimately, it falls down to three undeniable facts that all security organizations face as a reality.
You have a large and complex attack surface. Modern companies are sprawling digital ecosystems. The number of servers, services, applications, laptops, and cloud assets is enormous and constantly growing. It is impossible to protect every single component equally.
You have limited resources. No security team has an infinite budget or an infinite number of people. Crucially, your "asks" of the teams you depend on to change things, like Engineering and IT, are also a finite and precious resource. You cannot afford to spend your limited political and actual capital on protecting every asset with the highest level of scrutiny; you must prioritize.
Breach is inevitable. Given the first two facts, you must assume that attackers will eventually get past your outer defenses. The "secure all the things" approach is a recipe for failure. If you assume compromise, the most logical question becomes: "What are the things we absolutely cannot afford to lose once an attacker is inside?"
These three realities force a shift in mindset: from an unwinnable game of protecting everything on the perimeter to a focused, strategic mission of protecting what is most critical from the inside out.
“Insider, Outsider - What’s the difference?” - Caleb Sima
Creating Your Crown Jewels Strategy
A successful crown jewels strategy is built on a deep understanding of your business. Here's how to create one:
1. Identify Your Crown Jewels
The first and most critical step is to identify what your crown jewels are.
What is a Crown Jewel?
The "crown jewels strategy" is a method of identifying and protecting the most valuable assets within an organization. These assets, the "crown jewels," are critical to the company's success and competitive advantage. The modern application of the strategy is a proactive approach to business resilience and cybersecurity, focusing resources on protecting what truly matters above all else.
Your crown jewels can be tangible or intangible, and may include:
Intellectual Property: Patents, trademarks, copyrights, and trade secrets.
Data: This is often the most critical category. It includes customer data, financial records, and research and development data and credentials.
Systems and Processes: Proprietary software, manufacturing processes, and supply chain logistics.
People: Key employees with unique skills and knowledge.
Reputation and Brand: The trust and loyalty of your customers.
Beyond the Obvious: Unconventional Crown Jewels
When identifying crown jewels, it's easy to focus on primary data and systems. However, thier are areas that many companies forget are also crown jewels. Consider these examples:
Backup Systems: An attacker who compromises your backups can destroy them, making recovery from a ransomware attack impossible. Ransomeware anyone?
Social Media Management Systems: Control over your brand's voice is critical. A compromised account can cause immense reputational damage in minutes.
CI/CD Pipelines: These automated systems have broad access to build, test, and deploy code. A compromise is keys to the kingdom.
IAM Systems: The "keys to the kingdom." Control over systems like Okta, Azure AD, or your internal authentication services is paramount.
DNS Management: The ability to control your domain's DNS records means an attacker could redirect your website and email traffic, leading to massive disruption and phishing opportunities.
💡 The amount of companies that don’t have centralized DNS and rely on marketing to manage the myriad of external domains is mind blowing
How to Find Your Crown Jewels
Assemble a cross-functional team: Include representatives from all major departments (IT, engineering, finance, legal, operations, HR, etc.) to get a holistic view of the organization.
Brainstorm potential crown jewels: Ask a series of questions to guide the discussion:
What makes our company unique?
What gives us a competitive advantage?
What would cause the most damage to our business if it were lost, stolen, or compromised?
What assets are essential for our day-to-day operations?
💡An amazing question to ask is “What scares you the most?” the answers from engineering are always mind blowing
Prioritize your list: Not all assets
are created equal. Rank your list of crown jewels based on their importance to the business. Consider the financial, operational, and reputational impact of losing each asset. Share that list with your cross-functional team and have them review.
A company's business model is the ultimate guide for this process. For example, at Robinhood, critical path trading systems must be up and running at all times. If an attacker were to DDoS these systems or an insider were to cause damage to their availability, the company could lose hundreds of millions of dollars in minutes. Therefore, any system in the critical path of trading becomes a crown jewel for availability. In contrast, at Databricks, they are stewards of the world's enterprise data. Any leak or unauthorized access of that data is the most critical threat. Therefore, their datastores were identified as the #1 crown jewels, with a focus on confidentiality.
2. Assess the Threats: Focus on Intent, Not Tactics
Once you've identified your crown jewels, the next logical step is to understand the threats they face. However, be warned: approaching this as a traditional, broad threat modeling exercise can be a mistake. This is because most security efforts are focused on the wrong thing: the attacker's tactics.
As a first-time CISO, I learned this the hard way. The issue with comprehensive threat modeling is that you soon discover hundreds, if not thousands, of potential paths from an initial entry point to a crown jewel. The paths scatter in so many directions that the exercise becomes one in futility. This happens because you are chasing the attacker's tactics: the specific vulnerability they exploit, the malware family they use, the style of their phishing email. These tactics change constantly, and trying to block all of them is an infinite, unwinnable game.
A better approach is to focus on the attacker's intent. An attacker's intent is far more stable: they intend to steal your customer data, they intend to disrupt your service, they intend to get your source code. By identifying your crown jewels, you have already identified the targets of their intent.
This reframes the entire problem. Instead of asking "How do we stop every possible tactic?", you ask, "How do we protect the things they are trying to get to, regardless of the tactic they use?"
This is why you must focus your defenses as close to the crown jewel as possible.
Think of it this way: the classic defense-in-depth analogy is putting your gold in a safe, putting that safe in a protected room, and then surrounding that room with guards and walls. The mistake many modern enterprises make is putting all the guards and walls very far away from the asset, leaving the center wide open.
The crown jewels strategy flips this. Start by building the safe. Go as close as possible to the crown jewel itself and add protections there first. This approach truly "assumes breach." It doesn't matter whether the threat is an outsider who bypassed the perimeter or a malicious insider; the asset itself is hardened and protected because you focused on the attacker's ultimate intent.
3. Develop a Protection Plan: The Inside-Out Approach
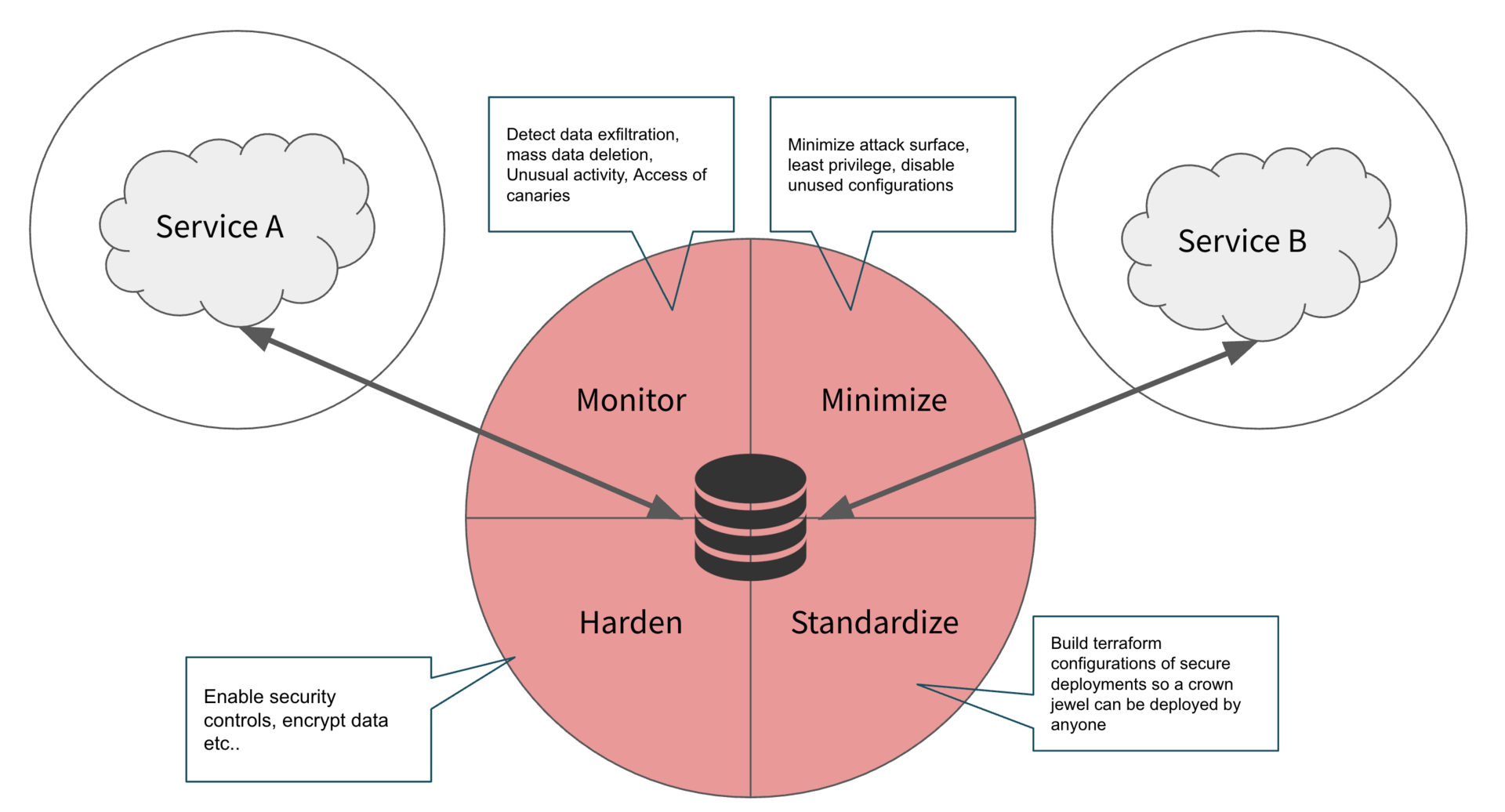
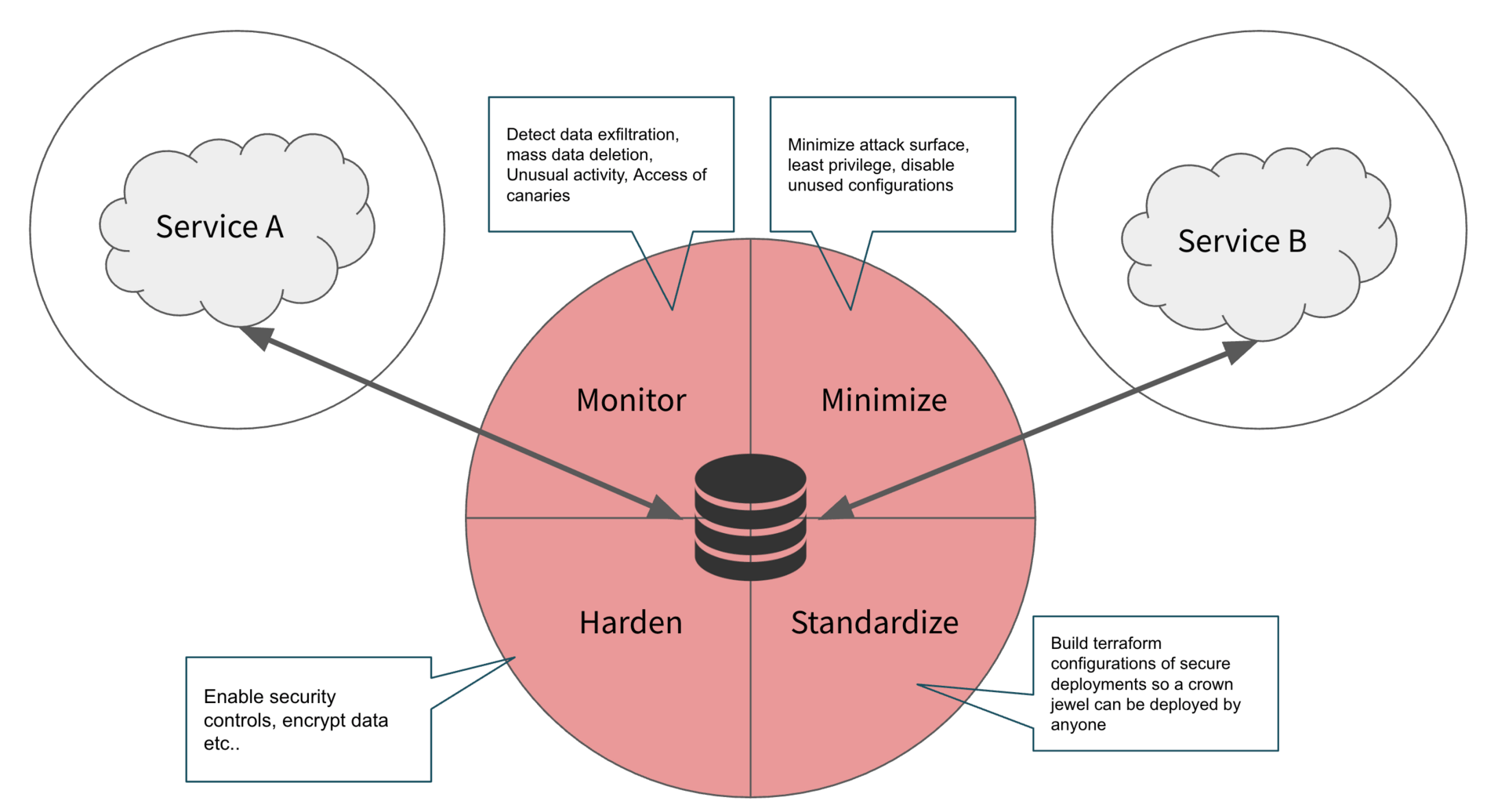
For each crown jewel, create a specific, multi-faceted protection plan. A proven method is the Inside-Out Approach. This philosophy dictates that you start your defensive efforts at the asset itself and work your way outwards, rather than focusing exclusively on perimeter defenses. It ensures that even if an attacker gets inside your network, your most valuable assets remain secure. This involves four key, continuous actions:
Harden: Strengthen the asset itself. This is your first and most important line of defense—the digital equivalent of building a strong safe for your gold. Hardening focuses on reducing the intrinsic vulnerabilities of the asset.
Example for a Datastore (e.g., a Database):
Encryption: Enable Transparent Data Encryption (TDE) to encrypt data at rest, and enforce TLS/SSL for all connections to encrypt data in transit.
Configuration: Disable default accounts, change default ports, and ensure the database software is patched and up-to-date.
Auditing: Enable detailed audit logging to track all access and changes to sensitive data.
Example for a Service/Container:
Base Image: Use minimal, hardened base images (like "distroless" images) that contain only the necessary libraries for your application.
Vulnerability Scanning: Integrate image scanning into your CI/CD pipeline to block deployments with known vulnerabilities.
Runtime Security: Run containers as a non-root user and use security contexts to restrict process capabilities (e.g., prevent privilege escalation).
Secrets Management: Use a dedicated secrets manager (like HashiCorp Vault or AWS Secrets Manager) instead of storing credentials in environment variables or config files.
Minimize: Reduce the potential ways an attacker can access the asset. Once the asset is hardened, you want to limit who and what can interact with it. This means shrinking the attack surface by enforcing the principle of least privilege, giving users and services only the access they absolutely need and disabling any unused or unnecessary configurations, network ports, or APIs. Every open door is a potential risk; the goal is to close as many as possible without impeding business function.
Monitor: Detection. You can't protect what you can't see. With the asset hardened and access minimized, you now need to watch the few remaining doors vigilantly. Implement robust monitoring to detect suspicious activities like data exfiltration, mass data deletion, or unusual access patterns. Using "canaries" (tokens or fake data) can help create high-fidelity alerts that immediately tell you when a secure area has been breached.
Standardize: Make security repeatable, easy, and the path of least resistance. The final step is to ensure that this high level of security can be applied consistently and automatically. The key to success is making the secure way the easy way for engineers. Provide pre-configured, hardened Terraform modules, secure base container images, and CI/CD pipelines that automatically handle security checks. When security is automated and integrated, it's not a blocker; it's just part of the default workflow, which dramatically increases adoption and reduces human error. The goal here is can a junior engineer technically spin up and create a new “crown jewel” and it by default is hardened, minimized and has the built in monitoring.
Moving Outward: Wash, Rinse, Repeat
Once you have applied this four-step process to the crown jewel itself, the work isn't done. The "Inside-Out" approach continues by moving to the next layer. Ask the question: Who or what connects to this asset? Is it a particular application, a specific system, or a group of people? This next layer of connected assets becomes your new focus. You then apply the same strategy: Harden, Minimize, Monitor, and Standardize that new layer. By repeating this process, you methodically build concentric rings of security, moving outward from your most critical assets.
4. Governance: Defining Roles and Responsibilities
A successful program requires clear ownership. Ambiguity leads to inaction. Establishing a simple governance model is critical to ensure accountability.
Business Owner: This is typically a VP or Director-level leader from the business or product side. They are ultimately accountable for the risk to the crown jewel. If a security control cannot be implemented for business reasons, this is the person who formally accepts that risk.
Technical Owner: This is the Engineering Director or Manager whose team builds and maintains the asset. They are responsible for implementing the security controls defined in the protection plan.
Security Team: The CISO's organization acts as the subject matter expert and program manager. The security team is responsible for advising on the correct controls, providing the tools to make implementation easy, and monitoring the program's effectiveness, but they do not own the risk itself.
Pitching the Strategy
Gaining buy-in for your crown jewels strategy is crucial for its success. You'll need to tailor your pitch to your audience:
To the Company Leadership
Focus on the business case: Explain how the strategy will protect the company's most valuable assets, reduce risk, and ensure business continuity. Give them the why.
Use data to support your arguments: Present statistics and comments from your cross functional exercise from the company and the potential impact of losing a crown jewel.
Be prepared to answer tough questions: The leadership will want to know about the costs, resources, and how is this going to help them either pass compliance or make them safer then their peers.
To Your Peers
Emphasize collaboration: Frame the strategy as a team effort that will benefit everyone.
Explain how it will make their jobs easier: A well-protected company is a more stable and successful company.
Ask for their input: Get their feedback early on the strategy as part of the pre-exercise in putting together the cross functional team.
To Your Team
Be clear and concise: Explain the strategy in simple terms and what it means for their day-to-day work.
💡What is great about this mission is that every part of a security org has a part to play. From 3rd party risk to security engineering.
Provide training and support: Make sure they have the knowledge and tools they need to follow the new security procedures.
Lead by example: Demonstrate your commitment to the strategy in your own work and repeat, repeat, repeat.
Implementation and Rollout: A Multi-Year Journey
A crown jewels program is not a one-off project; it's a multi-year strategy that matures over time. Structuring it with yearly and quarterly goals makes it manageable and demonstrates continuous progress. Here are some examples of how I did this.
Year 1: Foundation & Quick Wins
The first year is about establishing the framework and tackling the most critical assets to show immediate value.
Yearly Goal: Identify and secure the top 10% of crown jewels. Establish baseline metrics for the program.
Example Quarterly Goals:
Q1: Form the cross-functional team, finalize the top 5 most critical crown jewels, and define the initial protection plan templates.
Q2: Complete the "Monitor" and "Minimize" phases for the first 2-3 crown jewels. Deploy initial monitoring and canaries.
Q3: Complete the "Harden" and "Standardize" phases for the first 2-3 assets. Begin the full 4-step process for the remaining top 5 assets.
Q4: Present a "State of the Crown Jewels" report to leadership, showcasing the improved security posture of the top 5 assets with clear metrics.
Example KPIs & Metrics:
Objective: Identify Critical Assets.
KPI: # of crown jewels identified and prioritized. Target: 20.
Objective: Improve Security Posture.
KPI: % of top-tier crown jewels with a completed 4-step protection plan. Target: 100% of top 5.
KPI: Reduction in critical vulnerabilities for protected assets. Target: 90%.
Objective: Enhance Detection.
KPI: # of high-fidelity alerts generated from crown jewel monitoring. Target: Establish baseline.
Year 2: Expansion & Integration
The second year focuses on expanding coverage and beginning to secure the ecosystem around the primary crown jewels. The goal is to apply the 4-step protection plan to a significant portion of the remaining assets while also starting the "moving outward" process for the assets secured in Year 1. This involves mapping their connected systems and applying the same protection strategy to them, maturing automation, and improving incident response times for any alerts related to these critical assets.
Year 3 & Beyond: Maturity & Culture
Later years are about making the strategy a core part of the company's DNA. The focus shifts from initial implementation to achieving comprehensive coverage and embedding the strategy into the organizational culture. This is accomplished by integrating crown jewel security requirements into the default SDLC and focusing on standardization.
💡As in all things - there will only be a small percentage of your crown jewels that will make it to this stage. This is not about all crown jewels.
A Strategy Among Many
Of course, a crown jewels strategy is one critical mission that sits alongside others you may have. It provides focus but doesn't replace the need for broad security improvements. For example, in my role as CISO, I also had a 'safety hygiene' mission that focused on raising the levels of security fundamentals and basics across the entire company, alongside a dedicated 'least privilege' mission to systematically reduce access. All of these work in concert to create a robust security posture but they are all posts for another time.
Challenges and Considerations
While a crown jewels strategy is one of the most effective ways to focus a security program, it's not without its challenges. Being aware of these potential pitfalls is critical for a successful implementation.
Defining "Critical" Can Be Politically Charged: The process of identifying crown jewels is rarely a simple technical exercise. Different departments will inevitably argue that their systems are the most critical. Reaching a consensus requires strong leadership, clear business-driven criteria, and can be a significant political challenge.
The Perception of Neglect: When you announce you are focusing intense effort on the top 10% of assets, others will immediately ask, "What about the other 90%?" You must carefully manage the message that this is a strategy of prioritization, not one of neglect. It's about applying the right level of security everywhere, and the highest level where it matters most.
Burning Political Capital: Security teams have a finite number of "asks" they can make of Engineering and IT. A crown jewels program is a big ask. It requires significant effort from other teams to implement controls. If not managed well, this can strain relationships and exhaust the goodwill you need for other initiatives.
Risk of Impacting Agility and Performance: There is a real danger of "securing an asset to death." Applying too many restrictive controls can make a crown jewel difficult for legitimate users to access and operate, impacting business agility or system performance. This creates friction and can even encourage teams to create insecure workarounds. A constant balance between security and usability is required.
The Moving Target Problem: Business priorities change, and so do crown jewels. The critical asset of today might be deprecated tomorrow. The program requires a continuous cycle of re-evaluation and re-prioritization, which is a significant operational overhead that must be planned for.
Despite these significant challenges, a focused crown jewels strategy remains one of the most effective approaches for a modern security program. The alternative—trying to protect everything equally—is a guaranteed path to failure. The key is to view these challenges not as reasons not to pursue the strategy, but as the operational realities that must be managed with clear communication, strong partnerships with other teams, and a constant focus on the business's core mission. Being aware of these pitfalls is the first and most important step to successfully navigating them.
Final Thoughts
Returning to the feeling of being a new CISO, faced with the monumental task of "securing all the things" the crown jewels strategy offers a path through the chaos. It's not a magic bullet, but it is a coherent, defensible, and impactful plan that aligns security with the business. It transforms the security mission from an infinite game of whack-a-mole into a winnable campaign focused on what truly matters. It's a strategy that resonates with the board, empowers engineers, and, most importantly, makes life demonstrably harder for the adversary. By focusing on your most critical assets first, you build a foundation of resilience that can be expanded over time, turning an overwhelming responsibility into a manageable and measurable journey toward a safer company.